AWS Lambda prevent surprise bill from malicious actors (Denial of Wallet Attack)
The Problem
In simpler terms, consider you've built a digital doorway allowing people to use your online service. Before entering, each user has to prove they're not a robot, a task managed by another company's system. However, once they've proven their human status, what's stopping a person or malicious actor from repeatedly knocking on your door? Every knock costs you money, even if they don't gain anything meaningful from it.
From a technical perspective, the concern lies in using AWS Lambda functions for a web application. While bot checks, such as captchas provided by external services like Google, can prevent automated scripts from flooding requests, they don't prevent humans or malicious actors who have successfully passed these checks from bombarding the backend with requests. Each request to the AWS Lambda function incurs costs, presenting a risk of rapidly escalating charges if unchecked.
The Cost Implications
Each legitimate or malicious invocation of AWS Lambda translates to a cost. Malicious actors, aware of this, can exploit this system with a "Denial of Wallet" attack strategy. The term "Denial of Wallet" is a play on "Denial of Service" attacks, but instead of merely overloading services, the objective here is to exhaust financial resources and inflate operational costs.
Solutions Overview
Defending against these threats, especially those posed by determined human actors, demands a multi-faceted security strategy. Each layer of protection builds upon the previous one to provide a comprehensive shield against escalating costs.
Cloudflare for Bot Protection: The first line of defense is Cloudflare's bot protection, which can eliminate the majority of unwanted traffic by distinguishing between genuine users and potential threats.
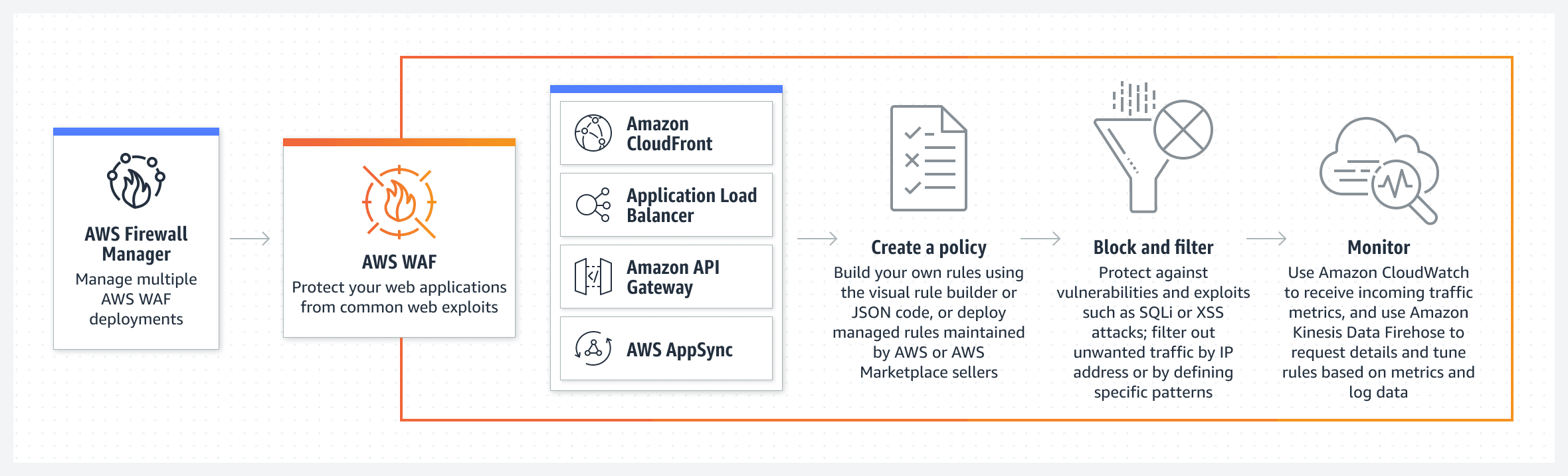
AWS WAF via API Gateway: For those persistent threats that get past the first line, AWS's Web Application Firewall (WAF) via the API Gateway can significantly mitigate a large portion of the remaining unwanted requests. Although AWS WAF could potentially serve as the primary defense layer, its higher price tag makes it a less economical first choice.
API Gateway Usage Plan + API Key: As a third layer, routing all partner requests through an API Gateway Usage Plan and an API Key proves beneficial. By setting generous yet reasonable limits, this layer ensures controlled access and keeps costs within the desired budget.
Budget and Usage Alarms: A reactive approach is equally crucial. Enhanced budget and usage alarms provide the necessary vigilance, ensuring that any abnormal spike in traffic or costs triggers instant notifications, allowing for swift intervention.
Additional Precautions
Placing the backend behind AWS WAF via the API Gateway offers an additional protective layer. Moreover, utilizing the API Gateway's throttling and quota capabilities can control the flow of incoming requests. This is particularly vital during a potential attack, ensuring that the rate of requests remains manageable and AWS Lambda costs do not skyrocket.
In Conclusion
In our ever-evolving digital landscape, staying proactive with security measures is paramount. A well-structured and layered defense mechanism doesn't just shield against threats; it is a cornerstone in effective cost management.